In today’s digital age, data security has become a top priority for individuals, businesses, and governments alike. With the increasing number of cyber threats, data encryption plays a critical role in ensuring that sensitive information remains secure. But what exactly is data encryption, and why does it matter? This comprehensive guide explores the fundamentals of data encryption, its types, applications, benefits, and the reasons why it is essential in today’s interconnected world.
What is Data Encryption?
Data encryption is the process of converting readable data (plaintext) into an unreadable format (ciphertext) to prevent unauthorized access. It involves the use of cryptographic algorithms and keys to encode information, ensuring that only authorized parties can decrypt and access the original data.
Encryption is used across various domains, including online banking, email communication, cloud storage, and secure file transfers. The fundamental purpose of encryption is to protect data confidentiality, integrity, and authenticity.
How Does Encryption Work?
Encryption works using mathematical algorithms and cryptographic keys. The basic process involves:
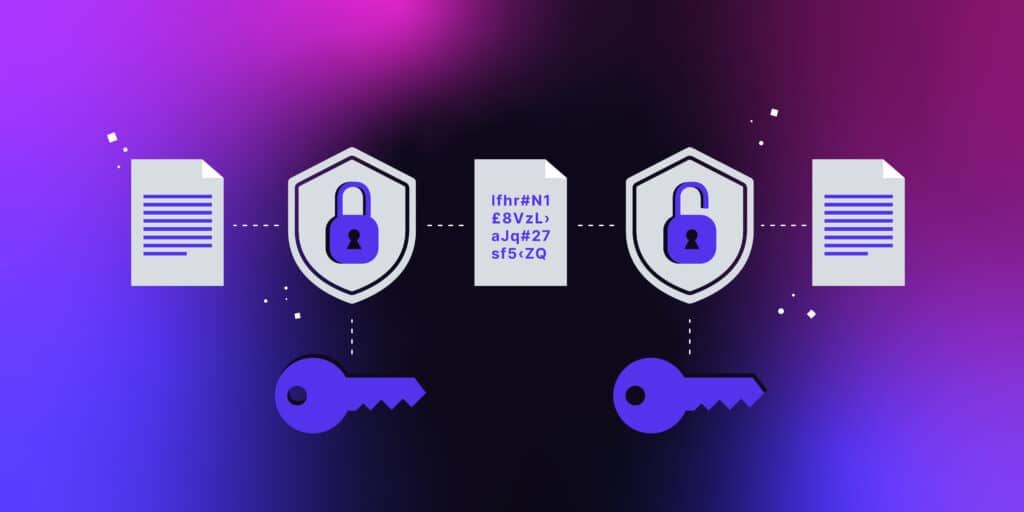
- Plaintext Input: The original, readable data that needs to be protected.
- Encryption Algorithm: A cryptographic algorithm processes the plaintext using an encryption key.
- Ciphertext Output: The algorithm produces an unreadable output known as ciphertext.
- Decryption: The recipient uses the appropriate decryption key to convert the ciphertext back to plaintext.
The security of encrypted data depends on the strength of the encryption algorithm and the secrecy of the cryptographic key.
Types of Data Encryption
Encryption techniques are broadly classified into two categories:
1. Symmetric Encryption
In symmetric encryption, the same key is used for both encryption and decryption. The sender and receiver must share the secret key securely before communication.
Examples of symmetric encryption algorithms:
- Advanced Encryption Standard (AES): Widely used for securing data across industries.
- Data Encryption Standard (DES): An older encryption standard, now considered weak due to advances in computing power.
- Triple DES (3DES): An improved version of DES with stronger security.
Advantages of Symmetric Encryption:
- Faster encryption and decryption.
- Requires less computational power.
Disadvantages:
- Key distribution is challenging as the key must be shared securely.
- If the key is compromised, security is breached.
2. Asymmetric Encryption
Asymmetric encryption uses two keys: a public key for encryption and a private key for decryption. The public key can be shared openly, while the private key remains confidential.
Examples of asymmetric encryption algorithms:
- RSA (Rivest-Shamir-Adleman): A widely used encryption algorithm in digital signatures and secure communications.
- Elliptic Curve Cryptography (ECC): A more efficient alternative to RSA, providing strong security with smaller key sizes.
- Diffie-Hellman Key Exchange: Used for securely exchanging cryptographic keys over a public network.
Advantages of Asymmetric Encryption:
- No need to share a single secret key, enhancing security.
- Ideal for secure online transactions and authentication.
Disadvantages:
- Slower compared to symmetric encryption.
- Requires more computational power.
Applications of Data Encryption
Data encryption is widely used in various sectors to protect sensitive information. Some key applications include:
1. Secure Online Transactions
Encryption is essential for securing online banking transactions, credit card payments, and e-commerce activities. Secure Sockets Layer (SSL) and Transport Layer Security (TLS) encryption protocols protect data transmitted between users and websites.

2. Email Security
Encrypted emails ensure that messages remain confidential and can only be accessed by intended recipients. Technologies like Pretty Good Privacy (PGP) and Secure/Multipurpose Internet Mail Extensions (S/MIME) provide robust email encryption.
3. Cloud Storage Security
Cloud service providers use encryption to protect stored data from unauthorized access. End-to-end encryption ensures that only the data owner can decrypt and access their files.
4. Data Protection in Communication
Messaging apps like WhatsApp and Signal use end-to-end encryption to secure conversations, preventing third parties from intercepting messages.
5. Healthcare Data Security
In the healthcare sector, encryption ensures the confidentiality of patient records, complying with regulations like the Health Insurance Portability and Accountability Act (HIPAA).
6. Government and Military Use
Governments and military organizations rely on encryption to safeguard classified information, ensuring national security and preventing cyber espionage.
Importance of Data Encryption
Data encryption is crucial for several reasons:
1. Protects Sensitive Information
Encryption prevents unauthorized access to personal, financial, and business-critical data, reducing the risk of identity theft and financial fraud.
2. Ensures Data Integrity
Encryption helps maintain data integrity by preventing unauthorized alterations. Even if an attacker intercepts encrypted data, they cannot modify it without detection.
The Impact of Cybersecurity Regulations on Businesses in 2025
3. Compliance with Regulations
Many industries have strict data protection regulations, such as GDPR, HIPAA, and PCI-DSS. Encryption helps organizations comply with these standards, avoiding legal penalties.
4. Prevents Data Breaches
In case of a cyberattack or accidental data exposure, encrypted data remains unreadable to attackers, minimizing the impact of data breaches.
5. Enhances Trust and Credibility
Businesses that implement strong encryption measures build trust with customers and stakeholders, ensuring that sensitive information is handled securely.
Challenges and Limitations of Encryption
While encryption is a powerful security tool, it comes with certain challenges:
1. Key Management
Securely storing and managing cryptographic keys is critical. If keys are lost or compromised, encrypted data becomes inaccessible.
2. Performance Overhead
Encryption and decryption require processing power, which can impact system performance, especially for large-scale data operations.
3. Complex Implementation
Implementing encryption correctly requires expertise. Improper configuration may lead to vulnerabilities.
4. Legal and Regulatory Constraints
Some countries impose restrictions on the use of encryption, requiring organizations to comply with local laws and regulations.
Future of Data Encryption
As technology advances, encryption methods continue to evolve to address emerging threats. Some key trends in encryption include:
1. Quantum Cryptography
Quantum computing poses a potential threat to current encryption algorithms. Researchers are developing quantum-resistant encryption techniques to counteract this risk.
2. Homomorphic Encryption
This advanced encryption method allows computations to be performed on encrypted data without decrypting it, enhancing data privacy in cloud computing and AI applications.
3. AI-Powered Encryption
Artificial intelligence is being integrated into encryption systems to improve security and automate threat detection.
What is Multi-Factor Authentication and Why It’s Crucial for Security
Data encryption is an essential component of modern cybersecurity, protecting sensitive information from unauthorized access and cyber threats. By understanding the different types of encryption, their applications, and their importance, individuals and organizations can implement robust security measures to safeguard their data. As technology continues to evolve, encryption will remain a cornerstone of digital security, ensuring confidentiality, integrity, and trust in the digital world.


Leave a Reply